Understanding OWASP top 10: How to use it as a standard
The OWASP Top 10, created by the Open Web Application Security Project (OWASP), is a critical resource for developers and organizations alike. This regularly updated list outlines the ten most critical web application security risks.
Understanding and leveraging the OWASP Top 10 as a standard is a powerful first step towards building and maintaining secure web applications.
What is the OWASP top 10?
The OWASP Top 10 is not an exhaustive list of vulnerabilities, but rather a curated selection representing the most prevalent and high-impact threats to web applications. These categories are derived from real-world data and expert consensus, ensuring their continued relevance in the evolving threat landscape.
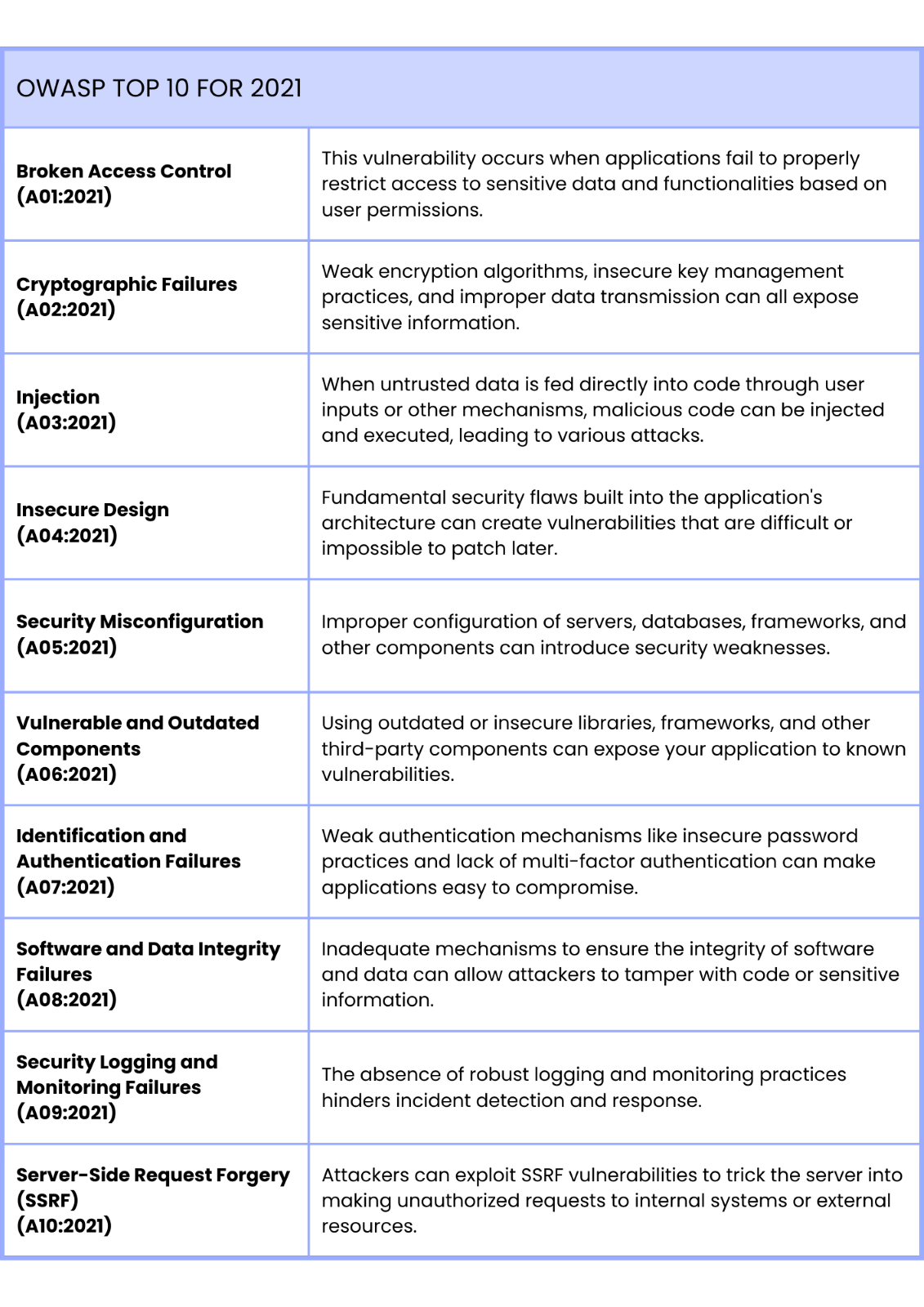
The current iteration, released in 2021, categorizes these risks as follows:
How to use the OWASP top 10 as a standard
The OWASP Top 10 serves as a foundational standard for web application security. Here's how you can leverage it effectively:
Security awareness: Use the OWASP Top 10 to educate developers, security professionals, and other stakeholders about the most critical web application security risks.
Threat modeling: Integrate the OWASP Top 10 into your threat modeling process to identify potential vulnerabilities early in the development lifecycle.
Secure coding practices: Encourage developers to adopt secure coding practices that mitigate the vulnerabilities outlined in the OWASP Top 10. This includes techniques like input validation, proper data sanitization, and secure use of cryptographic libraries.
Security testing: Utilize security testing tools and methodologies that target the specific vulnerabilities listed in the OWASP Top 10. This can include static application security testing (SAST), dynamic application security testing (DAST), and penetration testing.
Prioritization: The OWASP Top 10 is not ranked by severity, but you can use it to prioritize your security efforts based on the specific risks most relevant to your application and threat landscape.
Continuous improvement: The security landscape is constantly evolving. Regularly revisit the OWASP Top 10 to stay updated on the latest threats and incorporate them into your security practices.
Benefits of using the OWASP top 10 standard
By adopting the OWASP Top 10 as a standard, you can gain several advantages:
Reduced risk of attacks: Focusing on the most common and critical vulnerabilities significantly reduces the attack surface of your web application.
Improved development efficiency: Integrating security considerations early in the development process helps to avoid costly rework and delays later.
Enhanced compliance: Many security regulations and standards reference the OWASP Top 10, making it easier to achieve compliance.
Stronger security culture: Using a recognized standard fosters a culture of security awareness within your organization.
Conclusion
The OWASP Top 10 provides a solid foundation for web application security. However, for a truly comprehensive approach, consider these additional strategies:
Contextualization: Don't treat the OWASP Top 10 as a one-size-fits-all solution. Analyze your application's specific architecture, functionality, and data sensitivity to prioritize risks and tailor your security measures accordingly.
Integration with development lifecycle (SDLC): Weave security considerations throughout the entire SDLC. This could involve incorporating security champions into development teams, conducting regular security reviews, and automating security testing within your CI/CD pipeline.
Threat intelligence: Stay informed about the latest exploit trends and emerging threats by following reputable security resources and threat intelligence feeds. This allows you to proactively address new vulnerabilities and adapt your security posture.
Security champions: Empower developers to take ownership of security by creating a culture of shared responsibility. Train security champions within development teams to identify and address security risks during the development process.
Bug bounty programs: Consider implementing a bug bounty program to incentivize external security researchers to discover and report vulnerabilities in your application. This can be a valuable way to identify and address security issues you might have missed internally.
Metrics and measurement: Track your security progress by defining and measuring relevant security metrics. This could involve metrics like the number of vulnerabilities identified and remediated, the time to resolution for security incidents, and the overall security posture of your application portfolio.
It's important to understand that security is an ongoing process. Continuously learning, adapting, and improving your security practices can help you significantly reduce the risk of web application attacks and build a more secure and resilient IT infrastructure.