The hidden threat lurking in your system- Shadow APIs
APIs power everything—from web applications to mobile services, cloud platforms, and third-party integrations.
However, as organizations rapidly expand their API usage, a dangerous and often overlooked threat emerges: Shadow APIs. These are undocumented, unmanaged, or forgotten APIs lurking within an organization’s environment, exposing sensitive data and security vulnerabilities.
Unlike properly secured APIs, shadow APIs evade traditional security monitoring and governance, making them prime targets for cybercriminals.
In this edition of All Things AppSec, we explore the risks posed by shadow APIs, real-world breaches, and strategies to detect and mitigate these threats before they cause damage.
What are shadow APIs?
Shadow APIs refer to APIs that exist outside the scope of an organization’s official security policies. They may arise due to:
Untracked development: Developers creating and testing APIs without proper documentation or oversight.
Abandoned endpoints: APIs that were once used but left exposed due to poor lifecycle management.
Third-party integrations: External vendors introducing APIs without full visibility from security teams.
Cloud and microservices growth: Organizations rapidly adopting microservices architectures without comprehensive API governance.
These APIs create a significant attack surface, often containing direct paths to sensitive data and critical business functions.
Cybercriminals actively scan for shadow APIs to exploit vulnerabilities such as weak authentication, misconfigurations, and lack of encryption.
Real-world example: T-Mobile breach
In January 2023, T-Mobile revealed a data breach that had occurred in November 2022 due to an unmonitored API endpoint. This vulnerability allowed hackers to access sensitive customer data.
The attackers exfiltrated data from 37 million accounts, exposing personal details such as names, billing addresses, and email addresses.
What went wrong?
Lack of API visibility: The affected API was not actively monitored, making it an easy target.
Insufficient security measures: Weak authentication and access controls contributed to the breach.
Detecting and mitigating shadow APIs
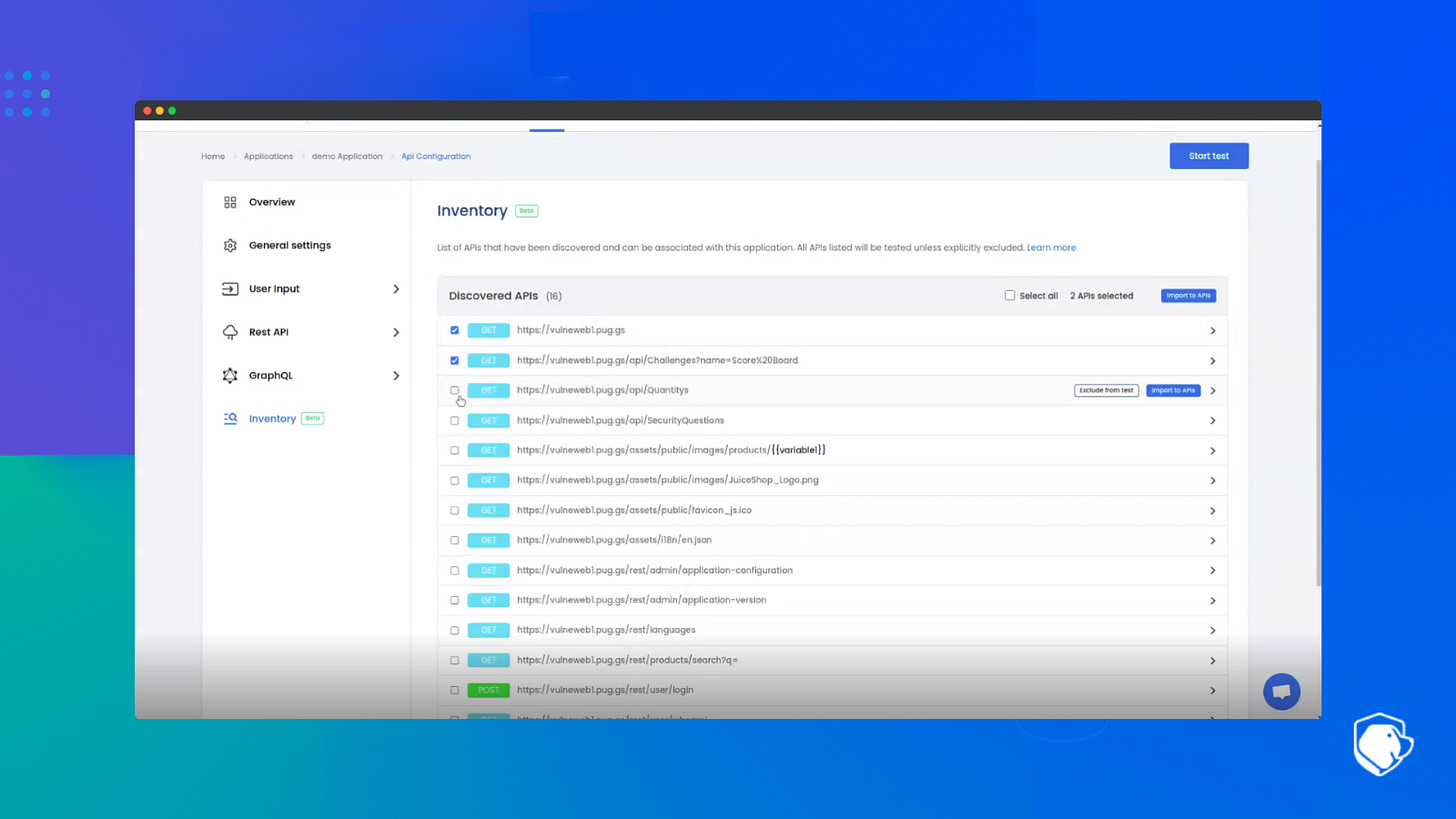
1. Inventory management
Organizations must maintain a real-time inventory of all APIs, including those developed by third-party vendors. Automated API discovery tools help detect unknown endpoints and ensure they comply with security policies.
🔍 Best practices:
Use API gateways to centralize API traffic.
Continuously scan networks for undocumented APIs.
Maintain an up-to-date API registry.
2. Strengthen API authentication and authorization
Many shadow APIs have weak or default credentials, making them easy targets for attackers. Implementing strong authentication measures can prevent unauthorized access.
🛡️ Security measures:
Enforce OAuth 2.0 and API keys for authentication.
Implement role-based access controls (RBAC).
Use Zero Trust security principles for API access.
3. Continuous API monitoring and threat detection
Since shadow APIs evade traditional security measures, behavioral monitoring is crucial to detect suspicious activities in API traffic.
🔨 Tools & techniques:
Deploy API security analytics to detect anomalies.
Use rate limiting and WAFs (Web Application Firewalls) to prevent abuse.
Conduct regular security audits of API logs.
4. Secure API lifecycle management
Security teams should ensure that APIs are properly managed from development to retirement.
🔄 Lifecycle steps:
Design phase: Security is integrated from the start.
Deployment: APIs undergo security assessments before going live.
Monitoring: Real-time logging and anomaly detection.
Decommissioning: APIs no longer in use must be removed.
How Beagle Security helps you tackle shadow APIs
Beagle Security provides an advanced API Discovery feature that helps organizations uncover and secure shadow APIs. Through automated scans and deep security analysis, Beagle Security ensures that no undocumented API goes unnoticed.
Key benefits of Beagle Security’s API Discovery:
Automated API detection: Identifies all active APIs, including undocumented shadow APIs.
Security testing: Conducts in-depth vulnerability testing on discovered APIs to detect potential risks.
Compliance assurance: Ensures that all APIs meet regulatory security standards like GDPR, HIPAA, and PCI DSS.
Seamless integration: Works with existing DevSecOps pipelines to enhance security workflows.
The future of API security
Shadow APIs are a silent but dangerous threat lurking within modern application ecosystems. Left unmonitored, they expand the attack surface, exposing sensitive data, violating compliance mandates, and enabling sophisticated cyberattacks. As organizations rapidly develop and integrate APIs, security must evolve beyond traditional perimeter defenses to ensure every API—documented or not—is accounted for and protected.
The key to tackling Shadow APIs is proactive discovery, continuous monitoring, and stringent security testing. Without full visibility, organizations are operating in the dark, leaving unknown entry points for attackers.
Key takeaways:
1️⃣ Shadow APIs are a growing security risk, often hidden from security teams.
2️⃣ They expose organizations to data breaches, compliance failures, and cyberattacks.
3️⃣ Strong API governance, authentication, and continuous monitoring are essential.
4️⃣ Organizations must adopt automated API discovery and Zero Trust principles.
Is your organization aware of its shadow APIs?