Hiding in plain sight: Vulnerabilities from business logic
Your security dashboard is green across the board. DAST scans passed, penetration tests came back clean, and your vulnerability management system shows zero critical findings.
Yet somehow, your e-commerce platform just lost $2.3M to customers who figured out how to stack discount codes and buy MacBooks for $50.
Welcome to the world of business logic vulnerabilities, the security flaws that hide in plain sight and turn your own business rules against you.
The $2.3M blind spot that's probably in your app right now
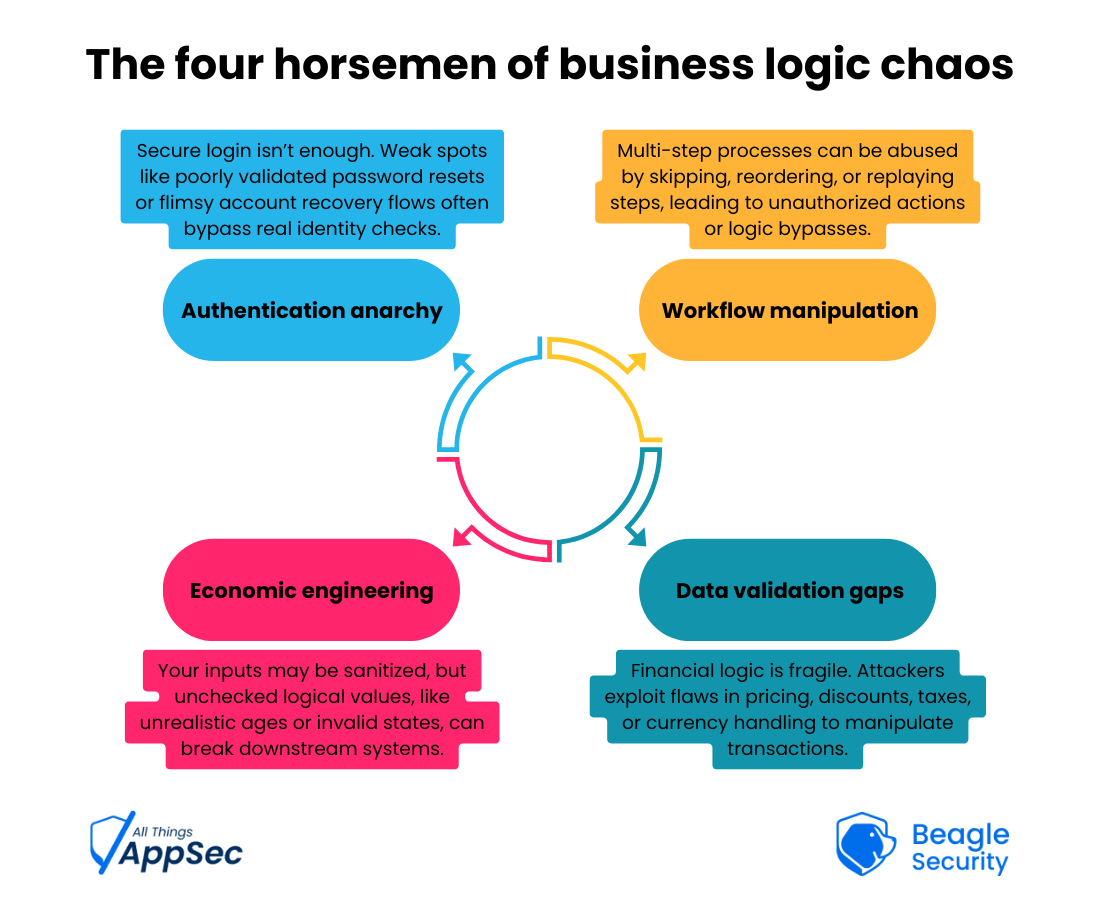
While security teams obsess over SQL injections and XSS attacks, business logic vulnerabilities are quietly draining bank accounts and exposing sensitive data through legitimate application features. These aren't coding errors; they're flaws in the business rules themselves.
Sort of like having a fortress with guards at every entrance but forgetting that anyone wearing a delivery uniform can just walk through the front door. Your security tools are checking if the walls are strong, but they're completely blind to whether your business logic makes sense.
Modern security platforms are getting better at detecting these complex vulnerabilities, but many organizations still rely on tools that were designed for simpler times.
Anatomy of a business logic attack
Reconnaissance (the not-so-exciting kind)
Attackers don't need to find buffer overflows or injection points. They just need to understand how your business works. They're reading your terms of service, testing user flows, and mapping business rules like any legitimate user would.
Edge case exploration
What happens if someone enters their birthday as tomorrow? Applies for a loan while simultaneously closing their account? Returns an item bought with a gift card that's now expired? These edge cases are treasure troves for logic flaws.
Exploitation through legitimacy
The attack doesn't look malicious. Customer service sees legitimate transactions. Monitoring systems detect normal API usage. Security alerts stay quiet. Everyone's happy except your balance sheet.
Why your security tools are missing the point
"No technical vulnerabilities found!"
"Application security looks solid!"
"Clean code, no obvious flaws!"
Meanwhile, your checkout process is hemorrhaging money because someone figured out how to manipulate your shipping calculator.
This isn't a criticism of the tools you have; they're excellent at finding technical vulnerabilities.
But business logic flaws exist in a different dimension entirely. They're not code problems; they're thinking problems that requires understanding both technical implementation and business intent.
Modern security platforms are evolving to bridge this gap by incorporating business context into their testing methodologies, but the detection challenge remains significant.
Detection strategies that actually work
Think like a con artist, not a hacker: Stop approaching security testing like you're looking for coding errors. Start thinking about how someone would abuse legitimate features. What would happen if users did exactly what you told them to do, but in the most inconvenient way possible?
The "impossible scenario" test: Design test cases around business events that shouldn't be able to happen: negative account balances, users completing workflows out of order, transactions that violate basic business rules. If it's impossible according to your logic, test it anyway.
Collaborative security reviews: The most effective detection combines security expertise with business knowledge. Regular reviews involving security teams, developers, and business stakeholders can identify potential logic flaws before they reach production.
Behavioral monitoring for business anomalies: Set up monitoring for business events that seem normal individually but suspicious in aggregate: multiple accounts from the same location, unusual transaction patterns, rapid-fire legitimate API calls that achieve illegitimate outcomes.
The uncomfortable truth about remediation
The remediation pain point: fixing business logic vulnerabilities often means changing business processes, not just code.
That discount stacking vulnerability? The fix might be "limit one promotion per customer," which could impact user experience and revenue.
Development team: "We can patch the technical implementation."
Business team: "But that change might hurt customer satisfaction."
Security team: "The current implementation is already hurting our bottom line."
These conversations require diplomacy, data, and a clear understanding of risk versus business value.
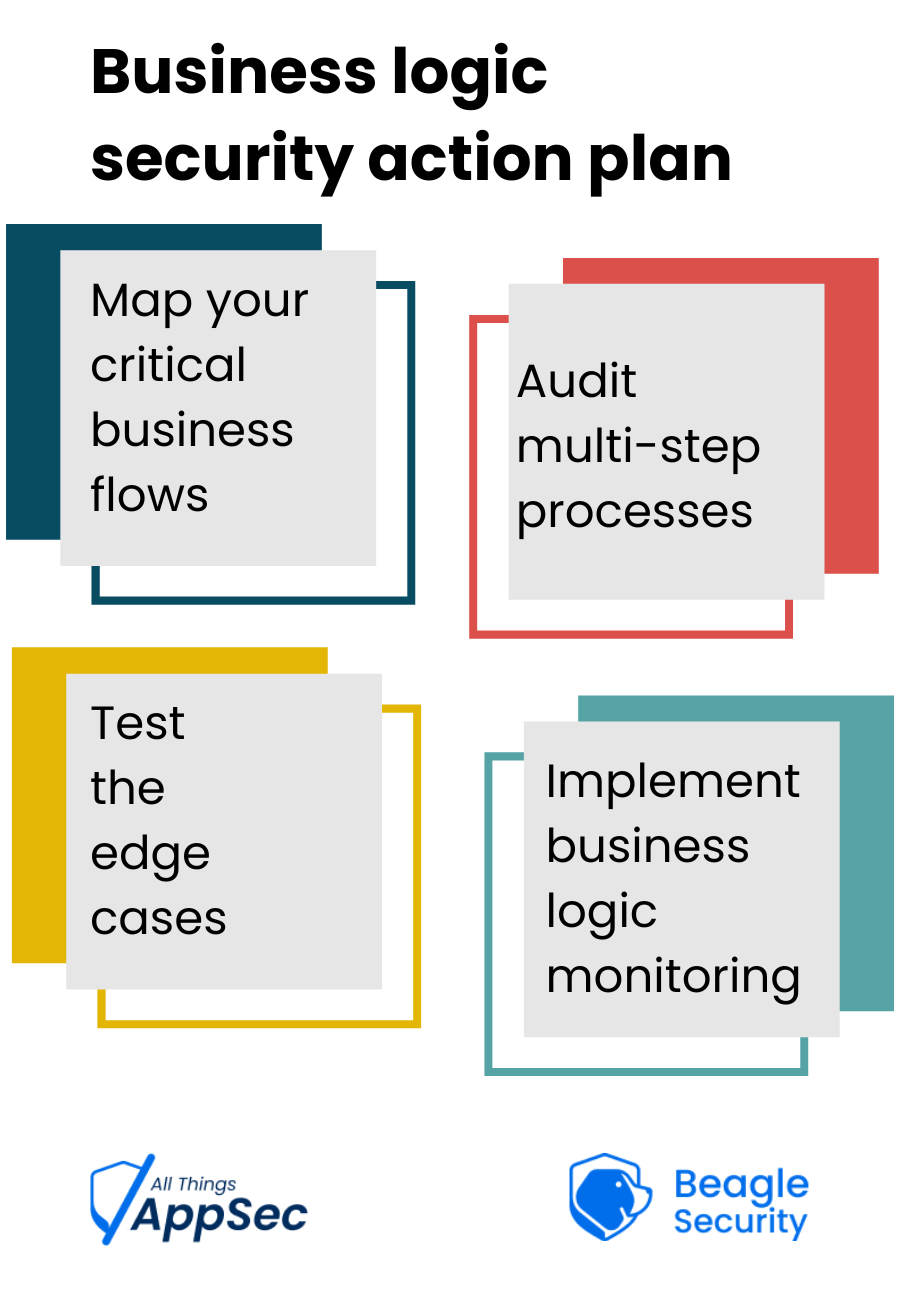
Your business logic security action plan
Map your critical business flows
Identify every process that handles sensitive data, financial transactions, or user privileges. Document the intended workflow and business rules for each.
Audit multi-step processes
Examine every workflow with multiple stages. Look for opportunities where users could skip steps, reverse order, or get stuck in intermediate states with elevated privileges.
Test the edge cases
What happens at system boundaries? During maintenance windows? When external services fail? Edge cases often reveal logic flaws that normal testing misses.
Implement business logic monitoring
Start tracking business events and patterns that could indicate logic exploitation: unusual transaction sequences, privilege escalations, or outcomes that don't align with business rules.
The evolution of business logic testing
Advanced security platforms are increasingly incorporating business context into their testing approaches. This includes understanding application workflows, recognizing business-critical functions, and testing scenarios that go beyond traditional technical vulnerability detection.
The future of application security lies in tools like Beagle Security that understand not just how applications work technically, but how they're supposed to work from a business perspective.
While traditional security scanners excel at finding technical vulnerabilities, Beagle Security takes a comprehensive approach to uncovering business logic flaws that other tools miss.
Taking action on business logic security
Business logic vulnerabilities represent a fundamental shift in how we need to approach application security. They can't be solved with better input validation or more secure coding practices alone – they require understanding the intersection of business requirements and security implementation.
Organizations that successfully manage these risks break down silos between security, development, and business teams. They implement testing methodologies that consider both technical and business context, and they use security platforms capable of understanding application behavior in business terms.
The good news? Awareness of business logic vulnerabilities is growing, and security platforms are evolving to address these complex challenges. The key is implementing comprehensive testing approaches that consider both technical security and business logic integrity.
What business logic vulnerabilities have you encountered in your applications? How are you adapting your security testing to catch these elusive flaws?