Authenticated vs unauthenticated scans: Learning the difference
The foundation of any robust cybersecurity strategy is understanding potential vulnerabilities within your systems. Vulnerability scanning plays a pivotal role in identifying these weaknesses, helping organizations address security risks before they can be exploited. However, a critical decision often arises during the scanning process: should you opt for authenticated or unauthenticated scans?
The choice between these two methods determines how your systems are assessed and the insights you gain from the process. Each has distinct characteristics, benefits, and applications, making it essential to understand their differences and when to use them.
This edition of All Things AppSec explores the nuances of authenticated and unauthenticated scans, guiding you to make informed decisions that enhance your security posture.
Understanding vulnerability scanning
Vulnerability scanning is the process of systematically inspecting systems, applications, and networks for security weaknesses. These scans help identify vulnerabilities such as unpatched software, misconfigurations, or insecure protocols that could serve as entry points for attackers.
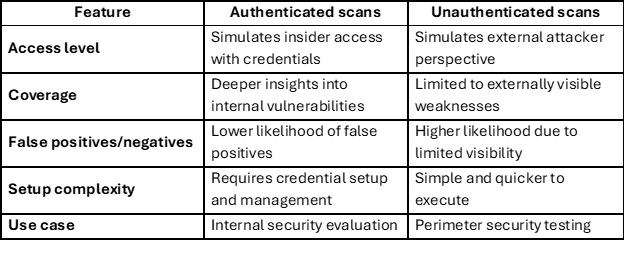
Vulnerability scans can be performed in two primary ways: authenticated and unauthenticated. The distinction lies in the level of access granted to the scanning tool.
What are authenticated scans?
Authenticated scans involve providing the scanning tool with valid credentials, such as usernames and passwords, to access the target system. These credentials allow the scanner to operate from an insider’s perspective, simulating what an attacker might see after compromising legitimate credentials.
Key features of authenticated scans:
Deeper insights: Authenticated scans can assess system internals, installed applications, and configuration files.
Privilege levels: Depending on the credentials provided, these scans can simulate different levels of user access, from standard users to administrators.
Accuracy: By accessing system internals, authenticated scans reduce the likelihood of false positives and negatives.
What are unauthenticated scans?
Unauthenticated scans, on the other hand, are conducted without providing the scanning tool with credentials. These scans simulate an outsider’s perspective, assessing vulnerabilities that could be exploited without prior access to the system.
Key features of unauthenticated scans:
External viewpoint: These scans evaluate the perimeter security and external-facing vulnerabilities.
Quick assessment: Without the need to establish credentialed access, unauthenticated scans can often be faster to deploy.
Baseline testing: They serve as a baseline to understand what an attacker without insider knowledge might discover.
Authenticated vs. unauthenticated scans: Key differences
Advantages of authenticated scans
Comprehensive coverage
Authenticated scans provide detailed insights into vulnerabilities, including those hidden within internal configurations, outdated software, and permission settings.
Realistic assessment
Since these scans mimic a legitimate user’s perspective, they can identify issues that would only surface during insider exploitation.
Proactive risk management
By revealing vulnerabilities that unauthorized users cannot access, authenticated scans enable organizations to proactively address risks before they escalate.
Advantages of unauthenticated scans
Ease of setup
These scans are straightforward to implement since they don’t require credential management.
External threat evaluation
Unauthenticated scans provide a realistic simulation of what external attackers might see, making them valuable for testing perimeter defenses.
Regulatory compliance
Many compliance standards require external vulnerability scanning to assess systems’ exposure to external threats.
When to use authenticated scans
Authenticated scans are best suited for scenarios requiring in-depth evaluation of internal systems. Use cases include:
Internal network security audits: To identify misconfigurations, outdated software, and improper access controls.
Compliance requirements: Many frameworks, such as PCI DSS, mandate internal scans to ensure compliance.
Post-breach analysis: Assessing vulnerabilities that may have been exploited using compromised credentials.
When to use unauthenticated scans
Unauthenticated scans are ideal for scenarios where the goal is to evaluate external security posture. Use cases include:
Perimeter security testing: To assess firewalls, web servers, and other public-facing infrastructure.
Preliminary security checks: For organizations initiating a security program, these scans can provide a starting point.
Regular monitoring: Continuous scans can identify new vulnerabilities exposed due to system changes.
Combining authenticated and unauthenticated scans
While each type of scan has unique strengths, the most robust security strategies incorporate both. Combining authenticated and unauthenticated scans ensures comprehensive coverage, addressing both external threats and internal vulnerabilities.
For instance:
Conduct unauthenticated scans regularly to identify new perimeter vulnerabilities.
Schedule authenticated scans periodically or after major system updates to assess internal risks.
Cross-reference findings to prioritize remediation efforts effectively.
Enhancing scans with Beagle Security
When it comes to maximizing the effectiveness of your vulnerability scanning, tools like Beagle Security provide a streamlined, AI-powered approach. Beagle Security supports both authenticated and unauthenticated scans, allowing organizations to tailor their testing to specific needs.
With easy integration into CI/CD pipelines and comprehensive test reports, Beagle Security simplifies vulnerability management. Its AI-driven insights help reduce false positives, making it a valuable tool for organizations seeking accurate and actionable results.
Additionally, Beagle Security's scheduling features make it easy to set up recurring scans, ensuring continuous monitoring of both internal and external systems.
Choosing the right approach
To determine whether authenticated or unauthenticated scans are right for your organization, consider:
Objective: Are you testing external defenses or internal systems?
Resources: Do you have the necessary credentials and permissions for authenticated scans?
Compliance: What type of scans are mandated by regulatory frameworks?
Aligning your scanning strategy with organizational goals and compliance requirements is the best way to make sure you make the most of vulnerability scanning.