Are you just checking boxes? (Compliance vs real security)
Regulatory compliance is often seen as the gold standard for security, but does ticking off a checklist truly make an organization secure?
Many companies focus on meeting compliance requirements rather than ensuring real, robust security.
While compliance frameworks like GDPR, HIPAA, and ISO 27001 set essential security baselines, they don’t always address evolving threats or sophisticated attack vectors.
In this edition of All Things AppSec, we explore the crucial differences between compliance and true security, the risks of a compliance-only approach, and how organizations can move beyond mere box-checking to build a resilient security posture.
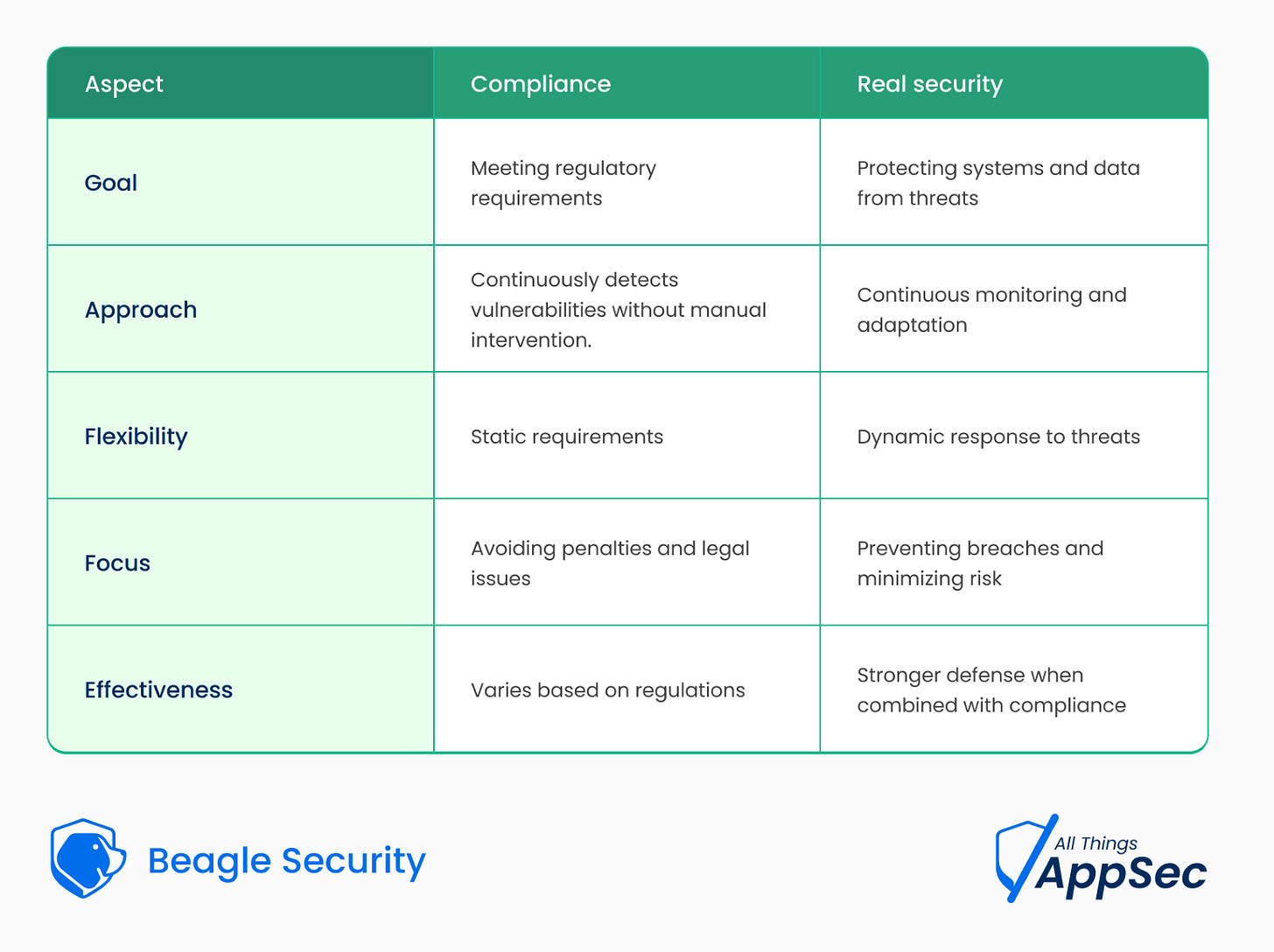
Understanding compliance vs. real security
Compliance refers to following specific security regulations, laws, or industry standards. These frameworks set minimum requirements that organizations must meet to operate within legal and contractual boundaries.
Compliance is often auditable and enforceable, providing accountability and guiding organizations toward structured security practices.
Real security, on the other hand, is about continuous risk management, proactive defense, and adaptability to emerging threats. It goes beyond meeting static requirements to actively protecting an organization’s assets, data, and systems against real-world attacks.
While compliance ensures organizations meet legal obligations, true security is about staying ahead of attackers—not just auditors.
The checkbox mentality: What it looks like
Many organizations fall into the trap of approaching security as a one-time project: conduct an audit, implement a few controls, pass the assessment, and breathe a sigh of relief—until the next audit cycle. This approach might satisfy regulators or stakeholders in the short term, but it rarely addresses the deeper vulnerabilities.
Signs of a checkbox approach:
Security measures are only updated before audits.
Policies exist on paper but aren’t practiced.
Risk assessments are rushed or templated.
There is no active threat monitoring or incident response planning.
In this setup, compliance becomes a box to tick, rather than a driver of real change or continuous improvement.
Why compliance isn’t enough
Compliance frameworks are designed to set a baseline. They are often created with a wide range of organizations in mind, meaning they are general and sometimes lag behind emerging threats. Just because you’re compliant doesn’t mean you’re protected against today’s advanced cyber attacks.
Consider this:
Compliance is static. Threats are dynamic. A system deemed secure during an audit could be compromised a week later.
Breaches happen even in compliant companies. Equifax was compliant with industry standards before its massive breach.
Compliance doesn’t guarantee awareness. Employees might follow rules blindly without understanding the underlying risks.
Real security is proactive, adaptive, and continuous
Security done right is not about checklists—it’s about mindset, culture, and continuous improvement. It involves understanding your unique threat landscape, adapting to it, and actively working to mitigate risk.
Here’s what sets real security apart:
Continuous monitoring: Regularly tracking systems and networks for suspicious activity.
Security-first development: Integrating security into the development pipeline (DevSecOps).
Employee training: Ongoing awareness and phishing simulations to empower staff as the first line of defense.
Threat intelligence: Staying updated on current and emerging threats specific to your industry.
Incident response readiness: Having a clear plan to detect, contain, and recover from attacks.
Bridging the gap: Compliance as a baseline, not the goal
So, how can organizations shift from a compliance-focused approach to a security-first mindset?
Start with compliance—but don’t stop there. Treat frameworks as the minimum standard, not the ceiling.
Invest in security testing. Regular penetration testing, red teaming, and vulnerability assessments go far beyond audit requirements.
Use real-world attack simulations. Tools like automated security testing can uncover gaps that audits often miss.
Prioritize risk over rules. Focus on your actual risk profile—not just the checklist.
Engage leadership. Security must be a board-level conversation, not just an IT issue.
How Beagle Security helps you move beyond checkboxes
At Beagle Security, we understand the pressure organizations face to stay compliant—but our mission goes deeper than that. Our platform helps you identify real-world security weaknesses before attackers can exploit them, ensuring your organization isn’t just meeting the standard but exceeding it.
Automated penetration testing to simulate real-world attacks.
API and web application security assessments that go beyond surface-level scans.
Continuous testing and alerts that adapt to changes in your applications.
Compliance mapping that aligns testing with regulations—but also flags non-compliance risks in real-time.
Whether you're preparing for an audit or looking to mature your security posture, Beagle Security gives you visibility, insight, and action—not just reports.
Wrapping up
While compliance is a necessary component of a secure organization, it is not the finish line—it's just the starting point.
Far too often, companies treat cybersecurity frameworks and standards as items on a checklist, focusing solely on passing audits rather than building meaningful security practices. This mindset leaves organizations vulnerable to modern threats that evolve faster than regulations can keep up.
Real security goes beyond policies and procedures—it’s about developing a culture of vigilance, proactive risk management, and continuous improvement. It means understanding your threat landscape, identifying vulnerabilities before attackers do, and ensuring that security is integrated into every part of your development and operations lifecycle.